Home Lab Network Redesign Part 1: The Remote Dedicated Server
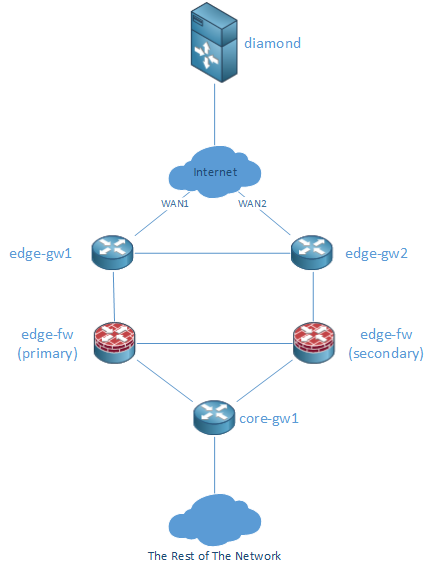
As promised, here is a very very basic diagram of my home lab. This is quite a high level overview of it, and the layer 2 information is not present as I suck at Visio, and all the connectors were getting messy on Visio with the layer 2 stuff present! What is not shown in the digram:
- There are two back-to-back links between the edge routers which are in an active-passive bond.
- Each edge router has two links going into two switches (one link per switch), both these links are in an active-passive bonded interface.
- The two edge firewalls only have two links going to each of those switches. One port is in the “inside” VLAN, and the other is on the “outside” VLAN. I wanted to have two links per VLAN, going to both switches, but the Cisco ASAs don’t do STP, or Port-Channels so I having two links would have made a loop.
- The link between the two ASAs is actually going through a single switch on a dedicated failover VLAN. From reading around, the ASAs go a little crazy sometimes if you use a crossover cable as the secondary will see it’s own port go down as well in the event the primary fails. It seems that this can cause some funny things to happen. Using a switch between them means that if the primary goes down, the secondary ASA’s port will still stay up avoiding any funniness.
- The core gateway only has two interfaces, each going two a different switch. One port is on the “inside” VLAN that the firewalls are connected to, and the other port is a trunk port with all my other VLANs. This isn’t very redundant, but I’m hoping to put in a second router when I have some more rack space and use HSRP to allow high availability.
As I mentioned in my previous post, I have a dedicated server hosted with Rapid Switch, through I wanted to route all my connections. There were a few reasons I wanted to do this:
- Without routing through the dedicated server, if one of my internet connections went down, and I failed over to the other, then my IP would be different from my primary line. This will mess up some sessions, and create a problem for DNS as I can only really point records at one line or the other.
- My ISP only provides dynamic IP addresses. Although the DHCP lease is long enough to not make the IP addresses change often, it’s a pain updating DNS everywhere on the occasions that it does change. Routing via my dedicated server allows me to effectively have a static IP address, I only really need to change the end point IPs for the GRE tunnels should my Virgin Media provided IP change.
- I also get the benefit of being able to order more IPs if needed, Virgin Media do not offer more than one!
- Routing via my dedicated server at Rapid Switch also has the benefit of keeping my IP even if I change my home ISP.
The basic setup of the dedicated server is as follows:
- There is a GRE tunnel going from the dedicated server (diamond) to each of my edge routers. Both GRE tunnels have a private IPv4 address, and an IPv6 address. The actual GRE tunnel is transported over IPv4.
- I used Quagga to add the IPv6 address to the GRE tunnels as the native Red Hat ifup scripts for tunnels don’t allow you to add an IPv6 address through them.
- I used Quagga’s BGPd to create a iBGP peering over the GRE tunnels to each of the Mikrotik routers, and push down a default route to them. The edge routers also announced my internal networks back to the dedicated server.
- I originally wanted to use eBGP between the dedicated servers and the edge routers, but I was having some issues where the BGP session wouldn’t establish if I used different ASNs. I’m still looking into that.
- There are some basic iptables rules just forwarding ports, doing NAT, and a cleaning up some packets before passing them over the GRE tunnel, but that’s all really.
Other than that, there isn’t much to see on the dedicated server. It’s quite a simple setup on there. If anyone would like to see more, I can post any relevant config.
Posts in this series
- Home Lab Network Redesign Part 2: The Edge Routers
- Home Lab Network Redesign Part 1: The Remote Dedicated Server
- Home Lab Network Redesign With Mikrotik Routers